Introduction
In this example you create a key pair on a Linux machine and convert the private key using PuTTY Key Generator so that it can be used in PuTTY and WinSCP for example. You could create the key pair on the PuTTY Key Generator, you don't need a Linux box for that. The Ubuntu Client here is the machine where the key pair is created and the Ubuntu Server is the machine where the public key authentication is enabled and that is being connected. The Ubuntu Client machine here is not really the client, we are using WinSCP on a Windows machine to connect the server. Also, PuTTY Key Generator is used on Windows.
There are probably numerous ways to do this and this is in no way the best practice (in the real life you being a Linux guru and all you would send the public key straight to the server machine's authorized_keys, and such fancy stuff), just a hands on example of one way to test the functionality.
See
Setting up SFTP server on Ubuntu how to set up an SFTP server on Ubuntu if you don't already have one running.
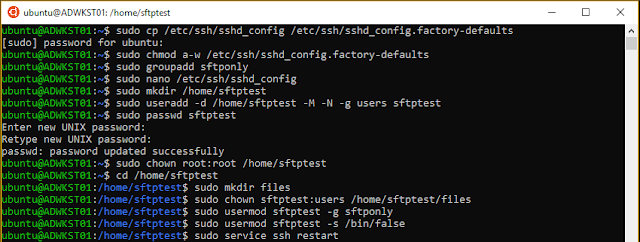
Enabling Public key authentication
On the Ubuntu Server use
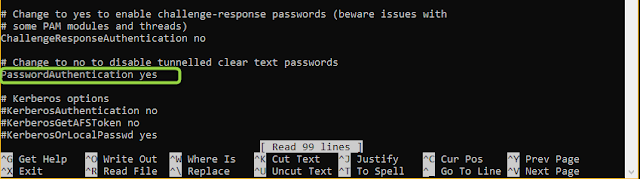
sudo nano /etc/ssh/sshd_config to edit the sshd_config -file. Set Pubkeyauthentication yes and you might want to set log level high in case you need to do debugging.
Save the changes with CTRL + O + [Enter] and exit the nano using CTRL + X
After the file has been modified use
sudo service ssh_restart to apply the changes.
The log file can be viewed with
sudo nano /var/log/auth.log

Creating a key pair
On the
Ubuntu Client enter the command to create a private key / public key pair:
ssh-keygen -t rsa
Hit [Enter] to use the default file name (id_rsa and id_rsa.pub).

Enter a passphrase for the private key (
you'll need this passphrase later when dealing with the private key, don't lose it):

Now you have created the private key and the public key to the /home/ubuntu/.ssh -directory. The whole process below:

Creating and editing the authorized_keys -file
The next step is to create
~/.ssh/authorized_keys file on the
Ubuntu Server machine for the sftptestpubauth SFTP user. First you need to create the
.ssh directory under the SFTP -user home directory and also create an empty
authorized_keys -file in the
.ssh directory.
Log into the
Ubuntu Server.
We are setting the public key authentication for one SFTP -user called
sftptestpubauth (you need to have the SFTP user created prior to this step, see my earlier post about the matter).
cd to the sftptestpubauth -user's home directory. With the command
ls -a you see that there is no hidden directories starting with the dot.

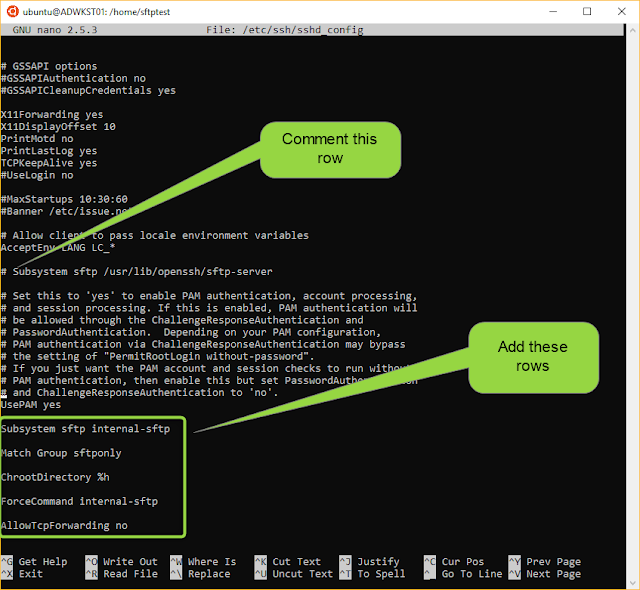
Make the .ssh -directory:
mkdir .ssh
The owner of the directory has all rights:
chmod 700 .ssh
Change owner to sftptestpubauth -user:
chown sftptestpubauth .ssh

cd to the .ssh -directory. If you cannot, apply
sudo -i -command to elevate and retry.
Create the authorized_keys -file:
touch authorized_keys

Set the rights and the owner:
chmod 700 authorized_keys
chown sftptestpubauth authorized_keys

You can check the rights and the owner with the following command:
namei -mo authorized_keys

Using and converting the files
On the Ubuntu Client machine, open the private key in nano:


Copy the text and put it in a file and save it as a PEM file (or use any extension, can be ppk if you like).

Open PuTTY Key Generator and load the PEM -file (you need to select 'all files' if you used PEM).
Enter the passphrase you defined earlier.


Copy the public key:

On the
Ubuntu Server machine in the
.ssh directory enter the command
nano authorized_keys
Paste the public key to the
authorized_keys -file (you could also use the public key from the
id_rsa.pub -file on the Ubuntu Client, the strings are different but they both work).

Use CTRL + O + [Enter] to write to file and CTRL + X to exit nano.
Save the private key.

In the WinSCP select the private key you saved in the PuTTYgen.

When you log in you need the passphrase. In PuTTYgen you can save the private key without a passphrase in which case the passphrase is not asked upon login.

You can use Pageant to remember the passphrases for the private keys you are using.

We did not use the original public key created on the Ubuntu Client machine in this example. The private key was converted to a new format and we used the new public key created in that process, but you could as well use the public key created on the Ubuntu Client.
Testing connection from the Ubuntu Client
On the Ubuntu Client go to the user home directory under which the key pair was created in the beginning. Enter the command:
sftp -i ./.ssh/id_rsa -P 22 sftptestpubauth@[myubuntuserver_name_or_ip]
The passphrase is asked and connection to the
Ubuntu Server is established.

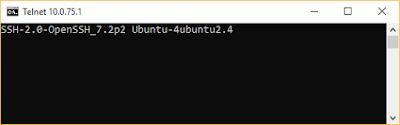
Testing connection from Windows using psftp
For Windows get the psftp from
here.